Windows Vista Ransomware Patch Download
Still stubbornly running an ancient version of Windows, despite the security threats? You're in luck, this time.
If the Windows users are using another antivirus software such as Trend Micro, Avast or AVG, should use the latest update and even confirm about their full protection against this massive threat. Download WannaCry Ransomware Patch for Windows XP, Windows 8, Windows Server 2003. There are two patches in general – one is meant for Windows 7 and Windows Server 2008 R2, the other patch is designed for Windows XP, Windows Vista, Windows 8 and Windows Server 2003. Installing these two patches will make sure that WannaCrypt or any other ransomware cannot make use of the SMB vulnerability to infect your PC. Windows XP Anti-WannaCry Ransomware Update KB4012598 Possibly Failing to Install Windows 10 migration to complete by year-end US Army Goes All-In on Windows 10 As WannaCry Infects More High. DOWNLOAD Windows Security Update for WannaCry Ransomware (KB4012598) 1.0.0.0 for Windows top alternatives FREE Avira Antivir Virus Definitions for Avira 10 and Older.
The ransomware attack known as WannaCrypt that sent organizations and individual users around the world scrambling for security cover has been addressed by Microsoft, the company behind the most widely used operating system on the planet, with a new software update. And, to the relief of many holding onto old versions of Windows, the update plays nice with some old school systems, too.
Late Friday, the company posted an official notice on its site regarding the update as well as general guidance regarding the WannaCrypt attack. The update covers users on Windows XP, Windows 8, and Windows Server 2003 (the attack didn't target Windows 10, according to Microsoft). Additionally, Microsoft advises users to 'use vigilance when opening documents from untrusted or unknown sources.'
The patch goes all the way back to Windows XP, a version of Windows Microsoft stopped supporting several years ago.
This update is particularly noteworthy because the patch goes all the way back to Windows XP, a version of Windows Microsoft stopped supporting several years ago. Regarding that unusual move, Microsoft's blog post states, 'This decision was made based on an assessment of this situation, with the principle of protecting our customer ecosystem overall, firmly in mind.'
'Today our engineers added detection and protection against new malicious software known as Ransom:Win32.WannaCrypt,' a spokesperson said in a statement emailed to Mashable. 'In March, we provided a security update which provides additional protections against this potential attack. Those who are running our free antivirus software or have Windows Update enabled, are protected.'
The new update is available here and those looking for more detailed information regarding WannaCrypt ransomware and how it may impact Windows can find it listed on the Microsoft security blog.
Microsoft provides an emergency update for unsupported Windows XP and Windows 8 machines in the wake of Friday’s WannaCry ransomware outbreak. Microsoft Releases XP Patch for WannaCry. Users of old Windows systems can now download a patch to protect them from this week’s massive ransomware attack. In a rare step, Microsoft published a patch for Windows XP, Windows Server 2003.
The rapid response from Microsoft indicates just how worrisome the ransomware attack has been for businesses around the world including vital organizations where computers are central to daily work such as hospitals and utility companies.
On Saturday, a report from Reuters indicated that the impact of the ransomware has been greatly reduced in recent hours due to the work of an unnamed UK-based researcher who worked to limit its spread.
The Locky ransomware is back, spreading via a massive wave of spam emails distributed by the Necurs botnet, but the campaign appears to be a half-baked effort because the ransomware is not able to encrypt files on modern Windows OS versions, locking files only on older Windows XP & Vista machines.
Windows 10 Ransomware
Locky's return to action is surprising but makes perfect sense. There have been numerous clues hinting that the same group behind the Necurs botnet was also behind the Locky ransomware, and more recently, the Jaff ransomware, which many have considered Locky's successor.
As Necurs slowly switched to Jaff, the Necurs group stopped spreading Locky spam in May, most likely preferring the newer Jaff ransomware instead of the older Locky.
Locky's return may be tied to Jaff's fall
The Necurs group's long-term plan was foiled last week after security researchers from Kaspersky Labs found a flaw in Jaff's encryption routine and created a free utility to help infected victims recover their files without paying the ransom.
This was unexpected, as researchers were never able to crack Locky's encryption method, and many thought Jaff to be just as tough, if not harder.
Windows Vista Ransomware Patch
Kaspersky's feat appears to have taken the Necurs group by surprise as well. As soon as the free decrypter was made available, Jaff spam went down, and beginning yesterday, the Necurs group started distributing Locky once more. This switch most likely happened because Locky's encryption was never cracked, and operators have a better chance of extorting ransom from infected hosts.
Windows DEP security feature mitigates new Locky variant
The new spam waves were detected by a large number of security researchers. All reported that they had trouble infecting themselves on their test machines.
It was Cisco's Talos division that discovered why. According to the company's experts, the Locky authors rushed to replace the decrypted Jaff version with Locky and made several errors in their deployment.
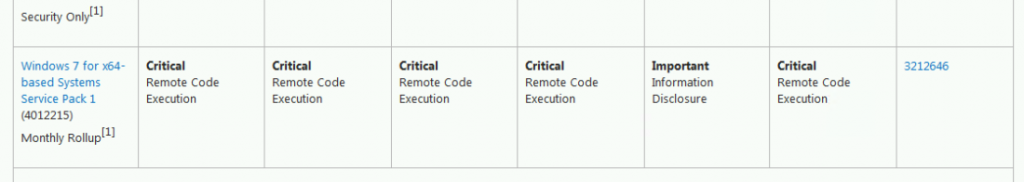
'Upon further investigation, we determined that on systems running Windows 7 or later with Data Execution Prevention (DEP) would cause the unpacker to fail,' said Cisco Talos experts. This means that only older OS versions such as XP and Vista are affected.
In their rush, the Locky authors most likely didn't notice this bug, as they put considerable resources into the ransomware's distribution, something they might not have done if they knew its ineffectiveness.
Locky spam accounted for 7.2% of all email spam
Cisco says spam for this new Locky variant accounted for nearly 7.2% of the Internet's entire email spam traffic. That's an insanely massive spam wave for a ransomware that only targets less than 10% of the entire Windows userbase.
Furthermore, this Locky version comes with minimal changes from the version researchers spotted the last time, in May. This Locky variant still uses the LOTPR extension at the end of encrypted files, and the same URL structure for C&C servers. This confirms the theory that the Necurs operators rushed to deploy Locky after Kaspersky published the Jaff decrypter.
Locky's new tactics
But there are also new wrinkles in this new Locky spam wave as well. Vitaly Kremez, Flashpoint Director of Research, discovered that Locky uses a new method of launching the infected binary on targeted hosts.
Still vetting but wanted to share -> #Locky has a seemingly new execution method using ddeexec & Shortcut execution via 'locky.exe' '%1' pic.twitter.com/61Ei0X4F6o
— Vitali Kremez (@VK_Intel) June 21, 2017In addition, the Locky spam emails use new texts for the email subjects and body content, albeit they still pretend to be invoices, payment receipts, order confirmations, and so on.
These emails also packed file attachments differently, utilizing a double-nested ZIP structure. The emails Bleeping Computer analyzed deliver a ZIP file with names in the format of eight random digits (e.g.: 38017832.zip). This initial ZIP file contains another ZIP file, which in turns contains an EXE file that runs Locky when executed.
Last but not least, this Locky version also added some anti-debugging protections that prevent the ransomware from running in virtual machines and other debug environments, which explains why researchers had a hard time analyzing it for the first few hours.
Overall, this particular Locky spam run seems to be a rushed effort, but we can expect the ransomware's operators to correct their flaws and start delivering a fixed version in the following days.
Below are other indicators of compromise for this latest Locky variant.
Hash:
Extension:
Ransom note:
Ransom Note:
Whitelisted folders:
Extensions: